Protecting your business from remote exploitation using Remote Desktop
Overview
Remote Desktop connections (sometimes referred to as Terminal Services or RDP) are a convenient way to remotely access and administer computers in your network. Readysell uses Remote Desktop to access customers’ servers to ensure your software is running as expected and to correct any issues, without having to interrupt your day-to-day operations.
But, if your system is not correctly configured, convenient remote access for yourself, your staff and Readysell can also mean convenient access to malicious third parties. Remote Desktop has been used as a vector for installing malicious software within networks, ranging from relatively benign crypto-currency mining through to full blown ransomware attacks.
The basics
At minimum, the following actions should be taken to ensure the security of your organisation to external breaches via Remote Desktop or SMB.
Ensure all users with Remote Desktop access have strong passwords
One of the ways third parties can gain access to your system is by just “guessing” the password of one of the users on your network. Based on research by SplashData the 25 most common passwords make up more than 10% of passwords. When picking a new password, make sure the password is not common, try it in Pwned Passwords at https://haveibeenpwned.com/Passwords. Do not use a password if it’s been used before.
Disable vulnerable SMBv1 protocol
This obsolete protocol has been leveraged in various malware attacks including WannaCry and Petya, which caused significant disruption in 2017. There’s a great guide at HowToGeek that explains how you can turn this off.
Secure your Remote Desktop endpoint
There’s a number of steps you should take, including:
- Moving Remote Desktop to a non-standard listening port
- Ensure NLA (Network Level Authentication) is enabled
- Ensuring the highest level of client encryption is enforced
Again, HowToGeek has come to the rescue with a guide covering how to complete all these steps.
Restricting remote access
The best thing you can do is to restrict access to Remote Desktop rather than leaving it open to the entire internet. There are multiple approaches to do this, including:
Whitelisting
Whitelisting means only allowing certain remote IP addresses to use Remote Desktop ports from the internet. This means creating a list of IP addresses that need access (including Readysell’s IP address – 110.175.89.111) and setting these up in your router or firewall. This is the simplest approach and works if you don’t need remote access to your server, or only access from the same static IP address each time.
Whitelisting Readysell's IP address using the Windows Firewall
The most basic way to achieve this is:
- Search for "Windows Defender Firewall with Advanced Security" in your Start menu
- Click "Inbound Rules"
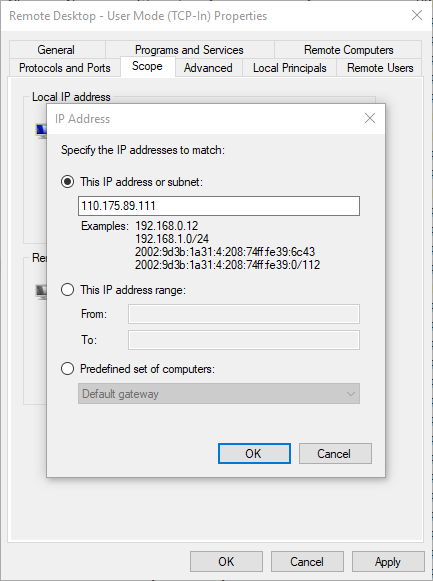
- Double click the rule you have set up for Remote Desktop - by default, this is called Remote Desktop - User Mode (TCP-In)
- Click the "Scope" tab
- Set the "Remote IP address" radio button to "These IP addresses"
- Click "Add..."
Add the address 110.175.89.111 and click "OK"
- Click "OK" to save your changes
Setting up a VPN
More technically difficult to set up, but works if you require access from various locations. Each user who needs to remotely access Remote Desktop will first need to connect to your VPN before access is possible.
If you’d like assistance with any of the above, please get in touch with Readysell Support and we’d be happy to help you out.